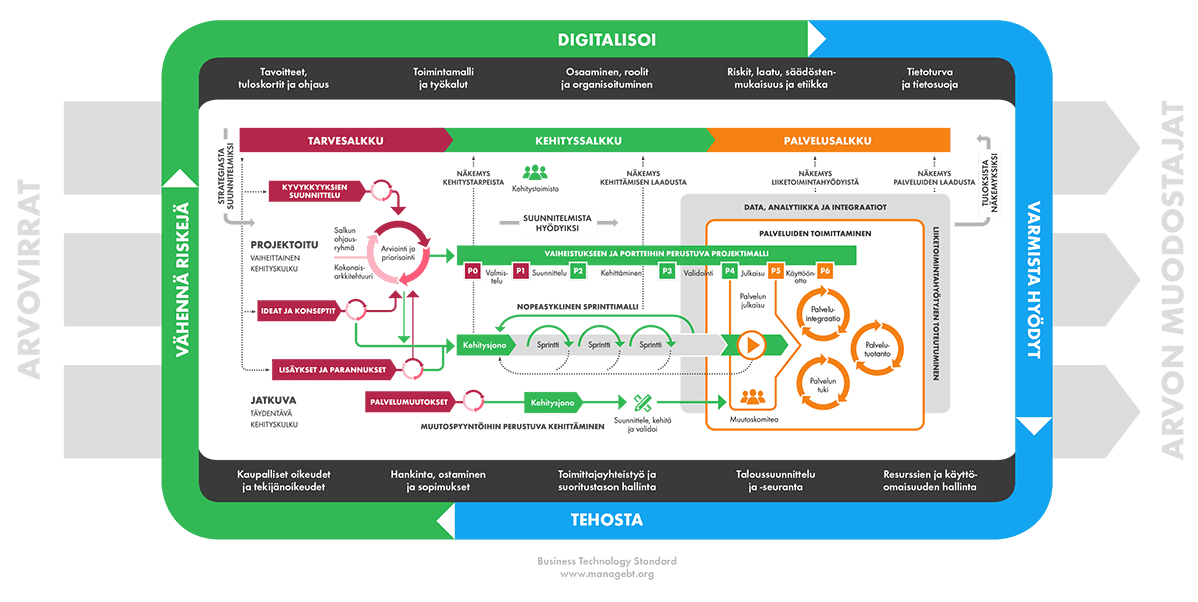
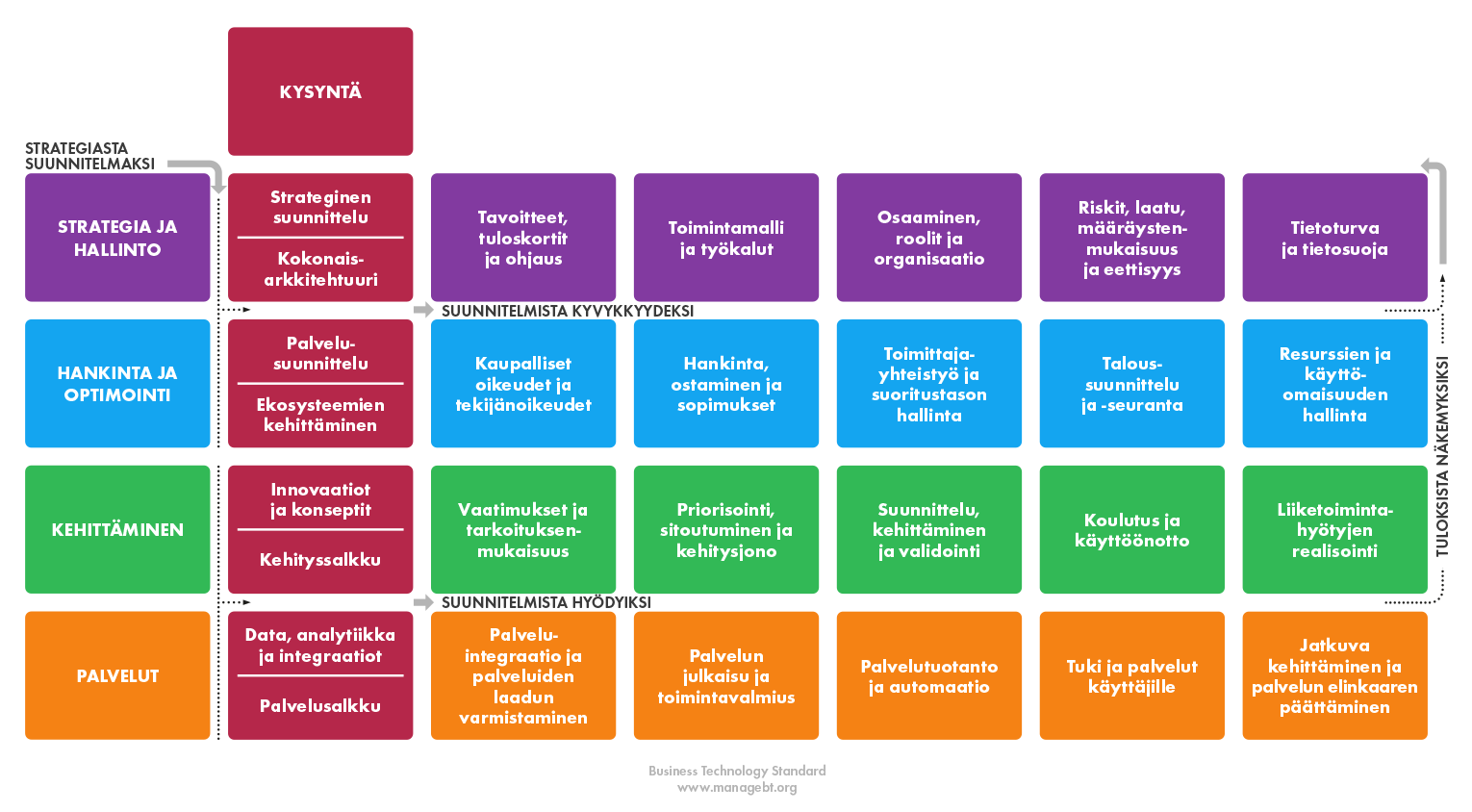
Bisnesteknologiamalli, tai lyhyesti BT-standardi, on avoin johtamisen viitekehys, jota voidaan hyödyntää informaatioteknologian suunnittelussa, rakentamisessa ja johtamisessa nykypäivän digitalisaation keskellä. Tämä on viitekehyksen neljäs, päivitetty versio, jonka sisältö on täysin uudistettu. Voit lukea BT-standardin eri osa-alueista valitsemalla haluamasi otsikon alla olevasta taulukosta. Lue lisää BT-standardista
Meillä on myös ChatGPT-pohjainen BTbotti, jota voit käyttää.
BT-mallin uusimmat päivitykset ja parhaat käytännöt kuulet webinaareistamme. Kuuntele nauhoitteet ja ilmoittaudu mukaan tuleviin webinaareihin:
BT Forum myöntää sinulle oikeuden käyttää muutoksitta BT-standardia johtamismallin ja siihen liittyvien hallintotasojen, johtamistasojen, käytäntöjen, roolien, toimintojen ja organisaatioiden suunnitteluun ja toteuttamiseen avoimen käyttöoikeussopimuksen mukaisesti. Bisnesteknologiamallin käyttöä rajoittavat kuitenkin immateriaalioikeudet. Mallin käyttöönottoa tukeva konsultointi on myös sallittua, kunhan mallin sisältöä ja merkitystä ei muuteta. Mallin muu käyttö, mukaan luettuna muun muassa mallin ja materiaalien julkaiseminen, malliin liittyvä koulutus tai konsultointi, edellyttää yhteistyösopimusta tai Business Technology Forum Oy:n kirjallista lupaa.
Kopioituun sisältöön tulee merkitä selvästi “Lähde: Business Technology Standard. Tekijänoikeudet omistaa Business Technology Forum”. Kaikki muut oikeudet pidätetään.
Tämä julkaisu sisältää materiaalia ja sisältöä, joka saattaa olla suojattu kolmansien osapuolten immateriaalioikeuksilla, kuten CMMI, ISO/IEC 20000, ISO 21500, ISO 38500, COBIT, DevOps, IT4IT, ITIL, PMBOK, PRINCE2, SAFe, SFIA ja TOGAF, kyseisten osapuolten käyttö- ja lisenssiehtojen mukaisesti.